Circuit Fingerprinting Attacks: Passive Deanonymization of Tor Hidden Services
A bipartisan agreement on crypto assets has a shrinking likelihood of passing as lawmakers enter an election year. We measure this across all listings and then take the average over the four week period, providing the average price change across product listings on the market. Join millions, easily discover and understand cryptocurrencies, price charts, top crypto exchanges and wallets in one place. While dark web monitoring is a broad term that covers different services at different companies, it can generally be defined as a service that monitors the dark web for signs of stolen data, whether it’s stolen personal information for identity theft or administrator credentials for corporate networks. A verified list of darknet markets and services with links for educational reference. WIRELESS THERMAL PRINTER TATTOO PRINTER. However, Nemesis does have categories set up for goods that won’t be as common on markets in 2022 because it is still a smaller market. Unless properly secured, mobile devices are a security and privacy nightmare. The networks are two mode network affiliation data that records all markets a vendor advertised stolen data products vendor by market and the dates they were recorded as listing these products. After the Hydra servers were shut down, most Hydra users organized in the RuTor forum.

Nemesis Vendor Analysis and Market Dynamics
Investigation was conducted with support and coordination provided by the Department of Justice’s multi agency Special Operations Division and the Joint Criminal Opioid and Darknet Enforcement JCODE Team. ProtonMail is a Swiss based encrypted email service that doesn’t require personal information when you sign up. So for packaging, that could be absolutely huge. In sum, drawing from past theoretical work that contends peers serve as important behavioural models from which to observe and learn offending behaviours, and more recent work that finds illicit market participants draw from their peers to assess the costs and benefits of illicit activities, we expect vendors’ peers to play an important role in shaping online behaviours. Compliant financial institutions, crypto exchanges, and other platforms that facilitate crypto transactions also use blockchain analytics tools to monitor and potentially block transactions flowing to or from darknet marketplaces. So, I was wondering if it is possible to call one of theses services. Whether on the clearnet or the dark web, using search engines and other browsing tools can lead to data leaks that expose your search history and other personal information. As we approach 2024, it is evident that the crypto industry is on the cusp of a significant transformation, driven by the entry of institutions and the democratization of finance on a global scale. While there is growth, commoditization is a spottier phenomenon than previously assumed. Darknet SecurityResearch. Aamir Lakhani, global security strategist and researcher at Fortinet, said that automation is key for monitoring the dark web, but he also cautioned against relying solely on such technology without human researchers and analysts. Step four: – when there is a description and the synchronization point is ready, the client provides an introductory message encrypted in the public key of the hidden service including the synchronization point address and the “one time” secret. Dont recomend this place. New dark web links for 2024, update. Further, drawing on past research that emphasizes disruptions increase vendor movement across marketplaces, we expect this relationship to strengthen following a law enforcement intervention. Distributed Denial of Service DDoS attack is an attempt to make an online service unavailable by overwhelming it with traffic from multiple sources. Keygens are available on the clear web as well. Additionally, HSI Baltimore special agents provided leads to international law enforcement partners resulting in the arrest of four additional co conspirators. Research output: Contribution to conference › Paper › Academic. Those that didn’t enjoy the first aren’t going to find anything new to draw them back. Reddit and its partners use cookies and similar technologies to provide you with a better experience. Most of them found that only a subset of accessible websites could be evaluated. Pertaining both methodologies to compile a sample in the context of research on Tor, they implicate substantial differences.
Are there any dark web markets which I can trust?
The quicker the payment is confirmed, the quicker the vendor will receive and be able to process your order. This network of more than 6,000 relays conceals the user’s Nemesis marketplace location from anybody engaging in online surveillance, as well as the websites visited. We do not support or encourage buying/selling illegal goods on dark web markets. The researcher also said that RuTor’s pro Ukraine and Kraken’s pro Russia stance showed us once again that geopolitical issues are also taking place in cyberspace. We use cookies to ensure you get the best experience. I get error that says something went wronf. Both are regular occurrences on the dark web. When accessing a website that uses an onion service, Tor Browser will show in the URL bar an icon of an onion displaying the state of your connection: secure and using an onion service. Have a question about Government Services.
Hand picked related articles
But I do at least want to point out that each mage is unique in several different ways; their breach setup, their starting hand, starting deck, unique ability and the cost to do said ability. The closure of these illegal markets resulted from the operations carried out a significant blow to the dark web activities. Box 10083INNISFIL, ON L9S 4B7. Copyright © 2010–2023, The Conversation Media Group Ltd. The market has evolved from a small, niche platform to its current status, marked by strategic expansions and innovations that have shaped its current stature in the marketplace. Crime displacement has been studied for decades, with much of this literature focusing on the impact of crime reduction efforts on the movement of crime to new areas Weisburd et al. The operators of several darknet markets with total sales of over a billion dollars have retired over the past year – marking a shift from the typical law enforcement takedowns and “exit scams”. Department of Justice950 Pennsylvania Avenue, NWWashington DC 20530. Scientific journals often put their articles behind a paywall or charge high fees for access, but Sci Hub offers open access to read or download research papers. Conf /etc/nginx/sites enabled/hideme. If you are trying to build a wholesale business to help balance your B2C sales, hell no. When I tried to call one of these services with his type, cli returns me this message : The passed service type is invalid with the type given by the previous command. If you wanna lose your money, give it to Nemesis. Chris was a PCWorld columnist for two years. Especially when using any public WiFi hotspots you should always use a VPN when accessing the Internet since you don’t know whether the access point is compromised. More recently, in October 2021, White House Market – the largest English language darknet market in operation at the time – announced its retirement. By accepting all cookies, you agree to our use of cookies to deliver and maintain our services and site, improve the quality of Reddit, personalize Reddit content and advertising, and measure the effectiveness of advertising. Both phenomena represent movement patterns, where an offender may move to additional sites to mitigate risk and expand their operations, and both phenomena increase the connectivity and dependency between marketplaces. In court documents, the Justice Department estimated that Hydra Market accounted for 80 percent of all cryptocurrency transactions on the dark net, generating $5. Pointed out that the Tor darknet is about half the size of the absolute number of onion services that exist. Tor Hidden Services – a Safe Haven for Cybercriminals. The market now has an established reputation among cybercriminals, which means that any stolen credentials for sale on there are likely to provide valid access to systems, services, or apps. POW + POS + No ICO or Crowdfunding means free coin distribution.

Money Laundering
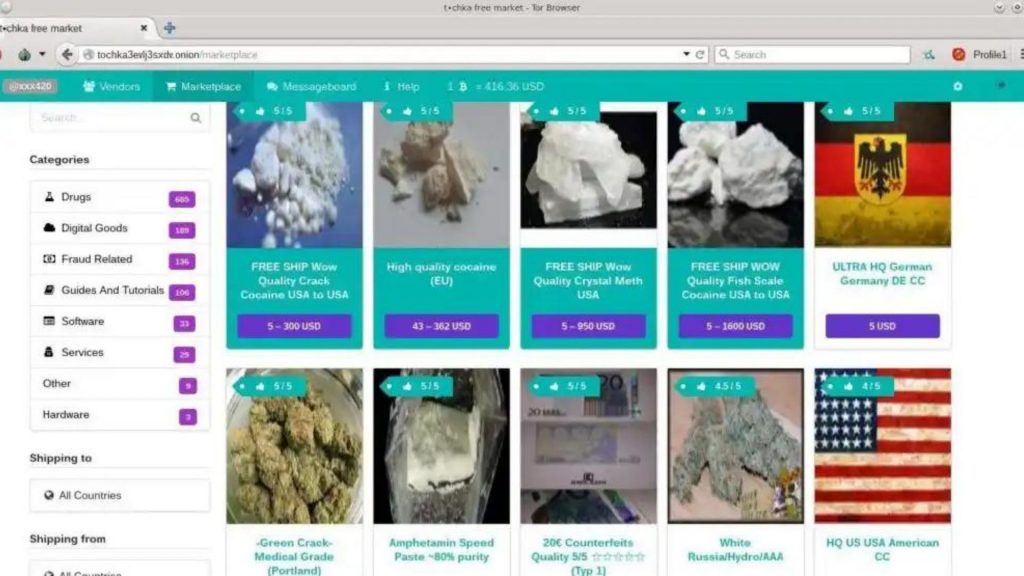
Big companies are working on projects for tokenizing individual subsidiaries. Though if you want, you can contact some of the mirror admins and try to convince them. And this is just a fraction of the illegal items available for purchase. The best dark web sites provide access to educational materials, host secure services, or bypass government censorship. As mentioned in Subsection 4. With your account created and mnemonic code saved somewhere safe, you can now proceed to sign in. Department of Justice Main Switchboard202 514 2000. The site requires that you create an account before you can explore it. The Flare platform continuously monitors your digital footprint and provides prioritized alerts to protect your company’s sensitive data and financial resources. This keeps you safe from any ISPs or authorities trying to detect Tor traffic. In 2014, Owen and Savage observed over 80,000 onion services within a period of 6 month. Thomas Trutschel / Contributor / Getty Images. Everything You Need to Know About DNS Attacks.
1 Answer 1
Nor is there any reliable way to differentiate between the “good guys” and the “bad guys”, making the existence of a backdoor a problem: how do you keep the bad guys from finding out about—and using—the backdoor. URL: 3g2upl4pq6kufc4m. Luxsocks – another market “affiliated” with UniCC – displayed what appeared to be a “takedown notice” posted by Russia’s Ministry of Internal Affairs. It uses a series of layered nodes to hide IP address, online data, and browsing history. Username or Email Address. For example, Dark Web markets have feedback and review sections, similar to what’s found on Amazon or eBay. 1, there are two main ways to collect onion addresses. The files are automatically encrypted, and the sender’s IP is not logged. Dream Market, Cryptonia and NightMare Market are already dead DNMs. Table 2 shows that vendor flows prior to the seizure of DarkMarket were guided by the number of vendors and prices. By accepting all cookies, you agree to our use of cookies to deliver and maintain our services and site, improve the quality of Reddit, personalize Reddit content and advertising, and measure the effectiveness of advertising. Get a Sample PDF of report —. For the first time, FBI agents from all the bureau’s field offices also visited buyers to tell them about the overdose danger of pills sold online, which are often disguised to look like prescription drugs. Aktuelle Marktdaten, Branchen News und Neuigkeiten von Next Kraftwerke mit unseren monatlichen Newsletter bleiben Sie auf dem Laufenden. 8, with a subsequent target surpassing $1. However, these transfers are held by distributed ledgers and are publicly available. Anonymous trading can occur through three different primary venues. A set of scripts to list tor hidden services. 2, short lived services can become a problem in the evaluation, as they may be overrepresented. Specifically, we conceive of marketplaces as a network in which individual e commerce sites are nodes, and the movement of sellers between sites are edges. So they’re buying the cheap products like fentanyl. These gains underscore Solana’s resilience in navigating the 2022 bear market, during which the crypto faced the threat of significant devaluation due to its association with the collapsed FTX crypto exchange. Wani MH, Paul RK, Bazaz NH, Bhat A.
Anonymous Market and Group Ties in International Trade
Want more content like this. And as is often the case on anonymous platforms, the tightest price wins. 108, Montreal, Quebec, H3K 1G6. Slide: The sheer volume of drugs seized during dozens of JCODE operations revealed both a flourishing market and the need for agencies to work together to fight it. Connect, learn, and engage with the web3 community on profile. When she’s not researching and writing about cyber security, you can find Elly on long dog walks, cooking a new recipe, or in the gym. Curated articles and papers on economics topics. Investigators also got leads from local police investigating overdose deaths, including a 19 year old man in Colorado who loved learning languages and building his own computers, said FBI Deputy Director Paul Abbate. These days, you often have to pass stringent verification and vetting processes to join a forum. It masks your IP address and traffic before you’ve even opened up the Tor browser. And it hides your IP address from hackers, your internet service provider ISP, and even government spies.
Threats
The table below shows the 20 streaming services whose hacked account credentials were most frequently listed for sale on the darknet markets. We then detail a mass longitudinal data collection effort to track vendor flows across multiple large scale marketplaces and the social network methods used to examine the connectivity of this darknet ecosystem. Note: if Maximum Supply is not available or limitless, Total Supply is used to calculate the value. I’m not sure what the technical limitations of rendezvous eavesdropping are, but if it were possible to capture. 2017 addressed such lack of information by presenting a study on: 1 automatic Tor Web exploration and data collection approaches, 2 the adoption of metrics to evaluate Tor data, 3 an in depth analysis of the hidden services graphs, and 4 a correlation analysis of hidden services’ semantics and topologies. Since Tor hidden services are part of the dark Web, they can be used for many illicit activities, as they provide a certain anonymity for its users. Looking for more ideas and insights. My method of payment is. Crafted by ©2023 UNITED THEMES™. Onion addresses and directs you to the anonymous service sittingbehind that name. The views, opinions and advice of any third party reflect those of the individual authors and are not endorsed by TMX Group Limited or its affiliates. The US is second, with around 18% of the share. She has a keen interest in topics like Blockchain, NFTs, Defis, etc. Researchers, on the other hand, follow a specific threat. I am selling on Faire and so far so good. Today web site screen shots below. EQS Group AG: Achim Weick, Tendering of 765,598 shares into the public takeover offer of Pineapple German Bidco GmbH at EUR 40. Website down for anyone else. In November 2023, CoinDesk was acquired by Bullish group, owner of Bullish, a regulated, institutional digital assets exchange. Extant related studies suggest that investment–stock price sensitivity increases with the amount of private information in stock prices. Com to find out more. If you value the privacy that Tor offers yourself and others, please make a donation today. Video conference results Q1 2023. A secure and stable platform—because where you trade matters. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. “The Hydra darknet site provided a platform for criminals who thought they were beyond the reaches of law enforcement to buy and sell illegal drugs and services,” said Chief Jim Lee of IRS Criminal Investigation. Hydra vendors offered a variety of illicit drugs for sale, including cocaine, methamphetamine, LSD, heroin and other opioids. This article was originally published at blog. Dark pools are sometimes cast in an unfavorable light but, in reality, they serve a purpose. “We shut down the original Silk Road website and now we have shut down its replacement, as well as multiple other ‘dark market’ sites allegedly offering all manner of illicit goods and services, from firearms to computer hacking.
Are you sure you want to delete this comment? This cannot be undone
Ahmia’s simple interface helps make searching the dark web more accessible, and Ahmia lets you perform deep web searches in regular web browsers like Google Chrome. The factors include growing institutional adoption of cryptocurrencies and DeFi or the arrival of new NFT projects. It’s just a blank box, so frustrating. Surprisingly enough, about 20% of daily users come from Russia. Descriptives of the darknet, and in particular of the Tor network, appear inconsistent and implausible in nature. Have you any professional opinions regarding recent enough solarwinds articles regarding their security breach. Now when you make a request to the web server and hit the Virtual Host that you created, the response should be from the remote server specified in your configuration. Statistics, search filters and news on K. There are, however, security issues involving Tor hidden services. DeepOnion is a cryptocurrency project that aims to provide its users with enhanced privacy and security features. Although Tails can run as a relay or hidden service, it requires data persistence see Chapter 3 and editing the Tor configuration file. — one of Congress’ chief crypto bill architects — is exiting Congress, leaving his crypto legislative drafts with an uncertain future. Treat your dedicated system like a work system: Only install the software necessary for your operations do not install anything for entertainment or other purposes. Check our Cookie Policy for more details. The column Method indicates which method was used to collect onion addresses. Considering the recent growth, Dark Web Markets will likely reach larger transaction volumes. Among the selection of tools and data hackers can buy here are dumps of stolen credit cards, stolen credentials, access to specific remote desktop protocol clients/servers, and stolen cookies. New hidden wiki updated for 2023. We’re trying to do our best to get the message out there that these pills are dangerous and you don’t know what you’re getting. At this point, it is very important that the hidden service adheres to the set of input protections required when creating new circuits.
About CyberGhost
No relationship is created with you, nor any duty of care assumed to you, when you use this blog. A Guide to the Silk Road Dark Web. Here are some examples of banner ads on the dark web. News and discussion about the Tor anonymity software. His contributions focus on expanding encryption tools, promoting crypto anarchist philosophy, and pioneering projects centred on leveraging cryptography to protect the privacy and political freedoms of others. I wish more retailers would understand what happens with Faire in the background. Consistent with the pre seizure network, the post seizure network consists of 17 markets, but they are better connected with a higher number of ties between them, 122 edges as compared to 95 edges before the seizure. Regulatory frameworks will grapple with issues like online fraud, money laundering, cybersecurity risks, and spam while fostering a culture of innovation. 2017 addressed such lack of information by presenting a study on: 1 automatic Tor Web exploration and data collection approaches, 2 the adoption of metrics to evaluate Tor data, 3 an in depth analysis of the hidden services graphs, and 4 a correlation analysis of hidden services’ semantics and topologies. It features a unique site design unlike any other market yet is still intuitive and easy to use. NCBI Literature Resources. One possible reason for this shift is that reputation has become an increasingly valuable commodity on the dark web. Search has a very interesting type of search engine where you can find vendors by their PGP fingerprint or Public PGP Key2. There’s so much of it, it would be really hard to run out of seaweed,” he said. All these metrics are used for determining active or passive projects despite the artificial hype. Since the war began, geopolitical dynamics have changed, and its reflection can be seen on the dark web. In order to gain insight into how these conflicting results are produced, the goal of this study is to review previous research on the matter with regard to terminology used, methodology of sample collection and the analysis of the data. Your email address will not be published. Therefore, the service randomly picks some relays, builds circuits to them, and asks them to act as introduction points by telling them its public key. Both individuals and organizations that work with arXivLabs have embraced and accepted our values of openness, community, excellence, and user data privacy. I commend the extraordinary investigative efforts of DEA’s Miami Counternarcotic Cyber Investigations Task Force, Cyber Support Section, and Special Operations Division, and the teamwork from federal and international law enforcement partners that led to this action. The project is still in its early stages, but the potential benefits of a well defined regulatory framework cannot be overstated. Prices range from as little as $10 to $500 or more for some data.
This website uses cookies
The first step, if you’re new to this space and want to facilitate a trade, is to buy yourself some cryptocurrency. AlphaBay was relaunched by DeSnake in August 2021 with a new design but with the same admin as before and is once again planning to become the biggest darknet market in history. While there is growth, commoditization is a spottier phenomenon than previously assumed. Being traders ourselves, we meticulously analyze over 100 brokers using real money, which grants us the expertise to evaluate the safety credentials of any given broker. You can choose from the contact options below or simply fill out the form to get in touch with us. For example, stocks must be listed with a national securities exchange before they can be traded on that exchange. EU based suppliers are important players in the darknet ecosystem, the evolution of which is shown in this timeline. Unfortunately, this entrance back into the internet from the Tor network poses a security and privacy risk. The shuttered sites were among the biggest on the dark web: over $1bn worth of goods and services have changed hands on AlphaBay since it launched in 2014. SUBSCRIBE TO OUR NEWSLETTER. The current study employs co integration analysis of wholesale monthly onion prices in selected marketplaces to determine the degree of market integration. In sum, our evidence is the first to shed light on the real effects of anonymous trading, which could be of relevance to policymakers in informing the debate on anonymous trading and to other market participants e. Public profiles for Economics researchers. Can You Still Use Windows 7 in 2020. Next Kraftwerke Belgium BV/SRLKoningslaan 107Gebouw/Bâtiment: Forest Factory1190 Brussel. This provides the ultimate in privacy sinceit’s being protected on both sides. Office of Public AffairsU.
Dark Web Monitoring
7 Interest on Bitcoin deposits will only be paid on balances of 5 BTC or less. They had a big update recently and a forum even better than dread. Without Informing the Preface and other participants of the STO service data identification network its public code, we do not want to disclose information about the location of thick skirt server its IP address. @Leopolde big vendors never answer anyone. If Tor configuration fails, configure it properly If all set, the script asks for input submit the file path containing onion URLs one URL in a line as input. If they can, more venues should play their part and reduce their maximum response time – lest ECNs be a place where additional hold times can cling on in the shadows. Keep your darknet PGP keys and other credentials limited to that system only, do not mix it with any activities that would expose your identity. Switch to the dark mode that’s kinder on your eyes at night time. The Infinity Forum launched in January 2023 as a forum founded by Killmilk, the former leader of the KillNet threat group, and comprised of members of Russian hacktivists and threat actors. Get it for PC, Mac, iOS. Our analysis showed that its operator may have retired as a Bitcoin billionaire, thanks to over $400 million in sales on the site, combined with the appreciating bitcoin price. According to the indictment, vendors on Hydra could create accounts on the site to advertise their illegal products, and buyers could create accounts to view and purchase the vendors’ products. Please note that our privacy policy, terms of use, cookies, and do not sell my personal information has been updated. However, the most striking ones regarding cybercrime in terms of numbers are DDoS for hire services, RDP accesses, and credentials. 045393 USD with a 24 hour trading volume of $143,156 USD. Currently, the market supports four cryptocurrencies: Bitcoin, Monero, Litecoin, and Zcash. Wow, so tiring to use the dark web without being exposed, but why do we need to log out of all our social media accounts before we continue. Interested in comic books more than academic papers. We can do this using the rm command in the terminal, as follows. Our current Round It Up partner is The Giving Tree. The market took more than 50% of the market share in April and May, reaching a peak of 65% on April 23. TRM provides blockchain intelligence to help financial institutions, cryptocurrency businesses, and public agencies detect, investigate, and manage crypto related fraud and financial crime. Markets Brace for Epic $11 Billion Crypto Options Expiry Event. Researchers, on the other hand, follow a specific threat. In reality though, you probably will want to segregate different servicesinto their own. By using the DropsTab. 9734/ajaees/2022/v40i121778. Download Avast SecureLine VPN to encrypt your internet connection and protect your privacy wherever you go online. Assistance was also provided by the Justice Department’s National Cryptocurrency Enforcement Team. 17% of the survey respondents are storeowners.
Glossary
This list may not reflect recent changes. Although part of that justmeans making sure your services support TLS, in this article, I describehow to go one step further and make it possible for yourusers to use your services completely anonymously via Tor hidden services. It’s also plentiful and comparatively cheap, said Notpla co founder Rodrigo Garcia. Naturally, this means independent and third party sellers can sign up and sell on the market. Does this recent surge of retirements signal the end of darknet markets. In a randomly compiled data set of 5,000 websites, we identified 558 addresses belonging to darknet marketplaces. Columbia Connection market. Markets, Tournaments, and the Matching Problem with Borrowing Constraints. There are sites that claim to offer content regarding human experimentation, secret government files neatly categorized in an online repository, exotic animal sales and many other hoaxes. VAT registration number 171021261.
